You are viewing an archival website from the original trustmark pilot in 2013-2016. If you are looking for more recent content about the trustmark framework, please visit the Trustmark Initiative website.
The Trustmark Framework is designed to support not only the issuance of trustmarks, but also their usage within the context of real-world systems. We describe on this page how a TR’s trustmarks can be bound to its live system endpoints and how TRPs can use the bound trustmarks in support of trust decisions about those endpoints. For this example, we assume that the systems are SAML SSO endpoints (IDPs and/or SPs); however, this general paradigm of trustmark binding is applicable regardless of the protocol(s) supported by the endpoints.
The diagram below illustrates how we bind trustmarks to a SAML Trust Fabric entry, also known as an Entity Descriptor. This is an XML document that contains metadata about a service endpoint. It is used by commercial and open source products to configure trust relationships prior to run-time.
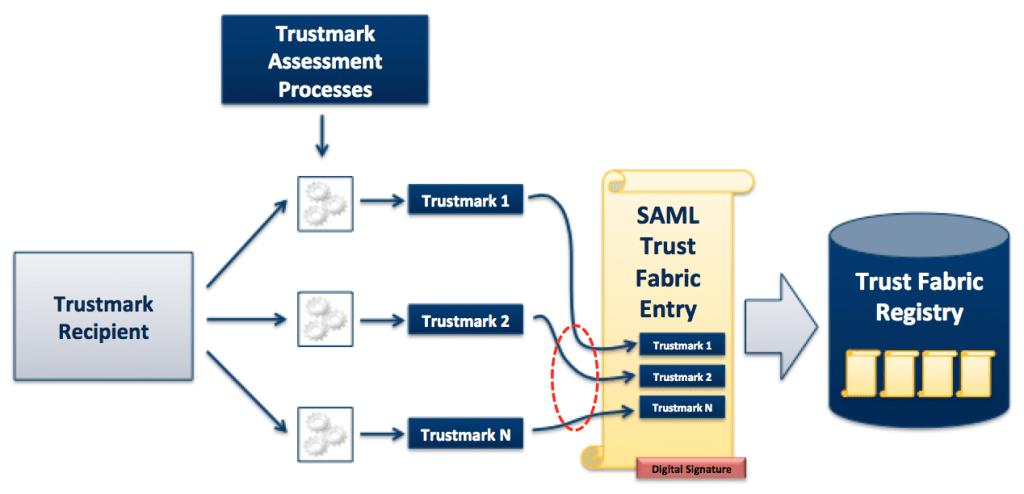
Trustmark Binding Example with a SAML Entity Descriptor
In this example, a TR first receives a set of trustmarks from a TP through the usual assessment process. Then the TR binds the trustmarks to the SAML Entity Descriptor (Trust Fabric entry) for an SAML SSO endpoint (IDP or SP) that it supports. Binding the trustmarks to the Entity Descriptor requires the following steps.
- The TR works with a Trustmark Binding Intermediary (TBI) to modify the Entity Descriptor, so that it contains either the trustmarks or pointers (URLs) to the trustmarks.
- The TBI attaches a digital signature to the Entity Descriptor to cryptographically bind the trustmarks to it. By signing the Entity Descriptor, the TBI effectively “vouches” for the legitimacy of the binding.
- The TR or the TBI registers the Entity Descriptor in a Trust Fabric Registry – also known as a Trustmark Binding Registry – which contains a set of Entity Descriptors with bound trustmarks.
At this point, the trustmarks have been bound to the Entity Descriptor, and it is ready for use by TRPs.
The following diagram illustrates how a TRP can use the Trust Fabric Registry to discover system endpoints (SAML SSO endpoints, in this example) that meet a specific trust policy.
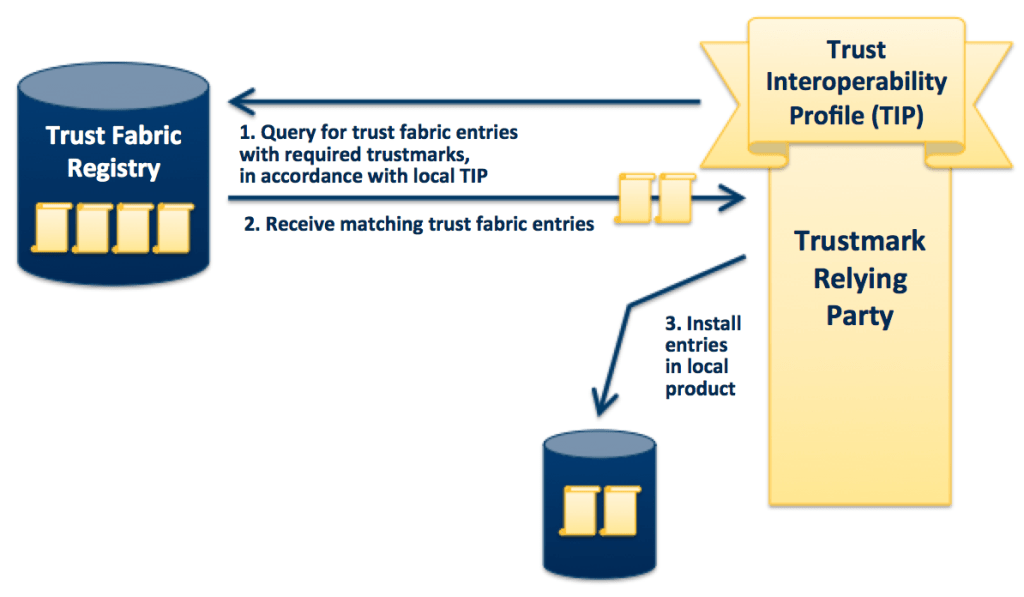
Trust Fabric Registry Query by a Trustmark Relying Party
The TRP uses the Trust Fabric Registry as follows.
- An administrator representing the TRP defines the TRP’s trust policy as a TIP. The TIP expresses the policy as a set of trustmarks that must be bound to an endpoint.
- The administrator submits a query to the Trust Fabric Registry on behalf of the TRP, along with the TIP. By doing this, the administrator is asking the registry to return any Trust Fabric entry that has a binding to all of the required trustmarks, as specified in the TIP.
- Upon receiving the results of the query, the administrator can further pare down the set of Trust Fabric entries, as needed, based on additional trust criteria required by the TRP.
- The administrator then installs the Trust Fabric entries in its local SAML product, thereby configuring the product to trust those endpoints.
We implemented trustmark binding in this manner for our pilot, with NIEF acting as both the TP and the TBI. To see how this works in an operational system, please visit the NIEF Trustmark Binding Registry.